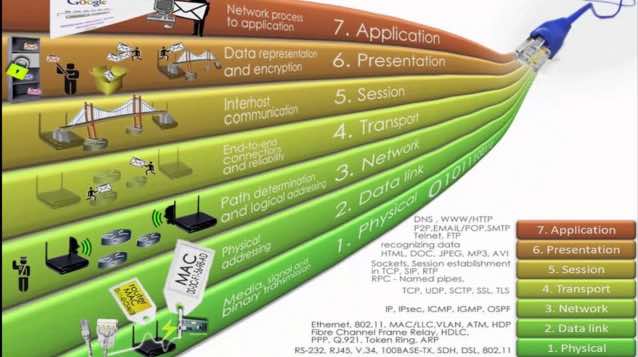
The Open Systems Interconnection model (OSI model) is a conceptual model that characterizes and standardizes the communication functions of a telecommunication or computing system without regard to its underlying internal structure and technology. Its goal is the interoperability of diverse communication systems with standard protocols. The model partitions a communication system into abstraction layers. The original version of the model defined seven layers.
A layer serves the layer above it and is served by the layer below it. For example, a layer that provides error-free communications across a network provides the path needed by applications above it. At the same time, it calls the next lower layer to send and receive packets that comprise the contents of that path. Two instances at the same layer are visualized as connected by a horizontal connection in that layer.
The model is a product of the Open Systems Interconnection project at the International Organization for Standardization(ISO), maintained by the identification ISO/IEC 7498-1.
Description of OSI layers
Recommendation X.200 describes seven layers labeled 1 to 7. Layer 1 is the lowest in this model.

Layer 1: Physical Layer
The physical layer has the following primary functions:
- It defines the electrical and physical specifications of the data connection. It defines the relationship between a device and a physical transmission medium (e.g., a copper or fiber optical cable, radiofrequency). This includes the layout of pins, voltages, line impedance, cable specifications, signal timing, and similar characteristics for connected devices and frequency (5 GHz or 2.4 GHz, etc.) for wireless devices.
- It defines transmission mode, i.e., simplex, half-duplex, full-duplex.
- It defines the network topology as bus, mesh, or ring is some of the most common.
- The encoding of bits is done in this layer.
- It determines whether baseband (digital) or broadband (analog) signaling will transmit the encoded bits.
- It primarily deals with raw data.
The physical layer of Parallel SCSI operates in this layer, as do the physical layers of Ethernet and other local-area networks, such as Token Ring, FDDI, ITU-T G.hn, and IEEE 802.11 (Wi-Fi), as well as personal area networks such as Bluetooth and IEEE 802.15.4.
Layer 2: Data Link Layer
The data link layer provides node-to-node data transfer—a link between two directly connected nodes. It detects and possibly corrects errors that may occur in the physical layer. It, among other things, defines the protocol to establish and terminate a connection between two physically connected devices. It also defines the protocol for flow control between them.
IEEE 802 divides the data link layer into two sublayers:
- Media Access Control (MAC) layer – responsible for controlling how devices in a network gain access to medium and permission to transmit it.
- Logical Link Control (LLC) layer – responsible for identifying Network layer protocols, encapsulating them, and controlling error checking and frame synchronization.
The MAC and LLC layers of IEEE 802 networks, such as 802.3 Ethernet, 802.11 Wi-Fi, and 802.15.4 ZigBee, operate at the data link layer.
The Point-to-Point Protocol (PPP) is a data link layer that can operate over several physical layers, such as synchronous and asynchronous serial lines.
The ITU-T G.hn standard, which provides high-speed local area networking over existing wires (power lines, phone lines, and coaxial cables), includes a complete data link layer that provides error correction and flow control utilizing a selective-repeat sliding-window protocol.
Layer 3: Network Layer
The network layer provides the functional and procedural means of transferring variable-length data sequences (datagrams) from one node to another connected to the same network. It translates logical network addresses into physical machine addresses. A network is a medium to which many nodes can be connected, on which every node has an address, and which permits nodes connected to it to transfer messages to other nodes connected to it by merely providing the content of a message and the address of the destination node and letting the network find the way to deliver the message to the destination node, possibly routing it through intermediate nodes. Suppose the message is too large to be transmitted from one node to another on the data link layer between those nodes. In that case, the network may implement message delivery by splitting the message into several fragments at one node, sending the fragments independently, and reassembling the fragments at another node. It may, but need not, report delivery errors.
Message delivery at the network layer is not necessarily guaranteed reliable; a network layer protocol may provide reliable message delivery, but it need not do so.
Several layer-management protocols, a function defined in the management annex, ISO 7498/4, belong to the network layer. These include routing protocols, multicast group management, network-layer information and error, and network-layer address assignment. The payload’s function makes these belong to the network layer, not the protocol that carries them.
Layer 4: Transport Layer
The transport layer provides the functional and procedural means of transferring variable-length data sequences from a source to a destination host via one or more networks while maintaining the quality of service functions.
An example of a transport-layer protocol in the standard Internet stack is Transmission Control Protocol (TCP), usually built on top of the Internet Protocol (IP).
The transport layer controls the reliability of a given link through flow control, segmentation/desegmentation, and error control. Some protocols are state- and connection-oriented. This means that the transport layer can keep track of the segments and retransmit those that fail. The transport layer also acknowledges the successful data transmission and sends the following data if no errors occur. The transport layer creates packets out of the message received from the application layer. Packetizing is the process of dividing a long message into smaller messages.
Although not developed under the OSI Reference Model and not strictly conforming to the OSI definition of the transport layer, the Transmission Control Protocol (TCP) and the User Datagram Protocol (UDP) of the Internet Protocol Suite are commonly categorized as layer-4 protocols within OSI.
Layer 5: Session Layer
The session layer controls the dialogues (connections) between computers. It establishes, manages, and terminates the connections between local and remote applications. It provides for full-duplex, half-duplex, or simplex operation and establishes checkpointing, adjournment, termination, and restart procedures. The OSI model made this layer responsible for the graceful close of sessions, a property of the Transmission Control Protocol, and for session checkpointing and recovery, which is not usually used in the Internet Protocol Suite. The session layer is commonly implemented explicitly in application environments that use remote procedure calls.
Layer 6: Presentation Layer
The presentation layer establishes context between application-layer entities, in which the application-layer entities may use different syntax and semantics if the presentation service provides a significant mapping between them. If a mapping is available, presentation service data units are encapsulated into session protocol data units and passed down the protocol stack.
This layer provides independence from data representation (e.g., encryption) by translating between application and network formats. The presentation layer transforms data into the form that the application accepts. This layer formats and encrypts data to be sent across a network. It is sometimes called the syntax layer.
Layer 7: Application Layer
The application layer is the OSI layer closest to the end-user, which means both the OSI application layer and the user interact directly with the software application. This layer interacts with software applications that implement a communicating component. Such application programs fall outside the scope of the OSI model. Application-layer functions typically include identifying communication partners, determining resource availability, and synchronizing communication. When identifying communication partners, the application layer determines the identity and availability of communication partners for an application with data to transmit. When determining resource availability, the application layer must decide whether a sufficient network or the requested communication exists. In synchronizing communication, all communication between applications requires cooperation managed by the application layer. This layer supports application and end-user processes. Communication partners are identified, quality of service is identified, user authentication and privacy are considered, and any constraints on data syntax are identified. Everything at this layer is application-specific.
Why you need to know the 7 OSI layers
Most people in IT will likely need to know about the different layers when they’re going for their certifications, much like a civics student needs to learn about the three branches of the US government. After that, you hear about the OSI model when vendors make pitches about which layers their products work with.
In a Quora post asking about the purpose of the OSI model:
“The purpose of the OSI reference model is to guide vendors and developers so the digital communication products and software programs they create will interoperate, and to facilitate clear comparisons among communications tools.”
-Vikram Kumar
While some people may argue that the OSI model is obsolete (due to its conceptual nature) and less important than the four layers of the TCP/IP model, Kumar says that “it is difficult to read about networking technology today without seeing references to the OSI model and its layers, because the model’s structure helps to frame discussions of protocols and contrast various technologies.”
Suppose you can understand the OSI model and its layers. In that case, you can also understand which protocols and devices can interoperate when new technologies are developed and explained.
The OSI model remains relevant.
In a post on GeeksforGeeks, contributor Vabhav Bilotia argues why the OSI model remains relevant, especially regarding security and determining where technical risks and vulnerabilities may exist.
For example, by understanding the different layers, enterprise security teams can identify and classify physical access, where the data is sitting, and provide an inventory of the applications employees use to access data and resources.
“Knowing where the majority of your company’s data is held, whether on-premises or in cloud services, will help define your information security policy. You can invest in the correct solutions that provide you data visibility within the proper OSI layers once you have this knowledge.”
-Vabhiv Bilotia
In addition, the OSI model can be used to understand cloud infrastructure migrations, particularly when securing data within the cloud.
And because the model has been around for so long and understood by so many, the uniform vocabulary and terms help networking professionals quickly understand about the components of the networking system:
“While this paradigm is not directly implemented in today’s TCP/IP networks, it is a useful conceptual model for relating multiple technologies to one another and implementing the appropriate technology in the appropriate way,”
-Vabhiv Bilotia
I couldn’t agree more.

How to remember the OSI Model 7 layers – 8 mnemonic tricks
If you need to memorize the layers for a college or certification test, here are a few sentences to help you remember them. The first letter of each word is the same as the first letter of an OSI layer.
From Application to Physical (Layer 7 to Layer 1):
All People Seem To Need Data Processing
All Pros Search Top Notch Donut Places
A Penguin Said That Nobody Drinks Pepsi
A Priest Saw Two Nuns Doing Pushups
From Physical to Application (Layer 1 to Layer 7):
Please Do Not Throw Sausage Pizza Away
Pew! Dead Ninja Turtles Smell Particularly Awful
People Don’t Need To See Paula Abdul
Pete Doesn’t Need To Sell Pickles Anymore