The Bitcoin network has a consensus of cipher-based agreements between all the actors involved. The consensus is that two people or more are highly involved in the process of the currency’s encryption and transaction verification.
The blockchain doesn’t run on its own. It requires a user base and network to continue its life. Two important people who help preserve this life are Alice and Bob, with their negotiations in private and public-key cryptography. Although metaphorically speaking, at times, these two are very much objective reality of the cryptocurrency system. Alice and Bob represent our systems’ security and basic protocol.
Also read: Future Use Cases for Blockchain Technology: Proper Decentralized Crowdfunding
Alice and Bob represent two archetypal characters in the range of cryptography. The names were first established by Ron Rivest in 1978 with his article “Communications of the ACM” to create ease and simplicity when talking about computational encryption. The names are also found in the book, “Applied Cryptography,” by Bruce Shneier, with other placeholder names mentioned as well. The names have common ground when trying to explain technical topics such as computational consensus, complex networks, and code framework.
Instead of saying, “ computer A sends a message to computer B”, the use of Alice and Bob are the main characters in applied cryptography, game theory, and physics. Developers and Coding theorists are concerned with the public and private lives of Alice and Bob working to protect them in theories and applied code. Coding theory contains the elements of source coding, channel coding, and secrecy coding. These are integral parts of the cryptography mission. With Alice and Bob, Rivest found a way to teach cryptography to the masses within a very basic form. Giving a broader understanding to the masses when explained in speaking engagements and on paper theorems.
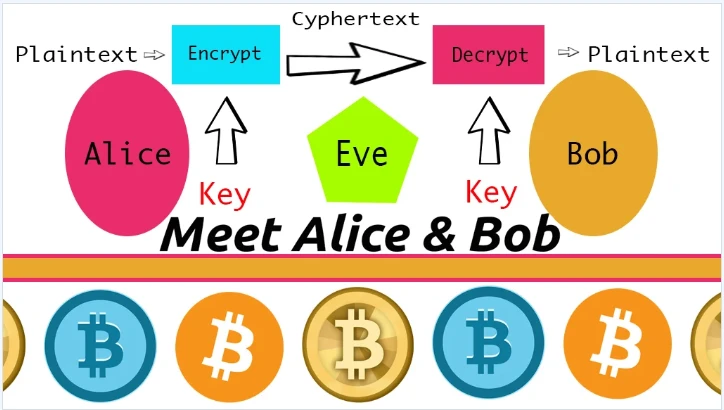
So what do Alice and Bob actually do? Alice and Bob represent two users or machines being used in key cryptography. Alice communicates a message to Bob, Alice then makes it important that Bob knows a secret number. Alice then sends Bob a random number, from which Bob forms a new number by encrypting the first under the second number, and sends the new number back to Alice. This process is called public and private key cryptography. The numbers shared between Alice and Bob are two uniquely related numbers that are compatible through mathematical equations. The public key is public, while the private key remains private throughout its ownership. The use of public and private key cryptography is very important in common parlance with the Bitcoin consensus network. Everyone agrees to play with Alice and Bob in the network.

When Satoshi wrote the “White Paper,” he wanted to make sure that Alice and Bob’s transactions could not be attacked by a third party. The third-party, we could refer to as “Eve,” cannot spend or access other parties’ bitcoins, because the digital currency is protected by Alice and Bob and the entire network’s actors. Transactions are kept safe by the encryption methods of public and private key cryptography set in place by these two important people and friends. Within the verification of constant transactions, the fabric of the group is continuously secured. With the Bitcoin network, details of all transactions are sent to all the placeholders or others in the group. When Bob sees his transactions held in the blockchain, he can be sure that Alice has sent her message to the network preventing duplicate transactions. This is a very important part of the Bitcoin protocol, as Alice would need to collaborate with friends or become herself more powerful than over half the network.
The three critical parts of a Bitcoin transaction require a form of “Ownership.” The process goes as follows: A user will broadcast to the network that they would like to move their possessed Bitcoins. The user must identify with the group represented by the blockchain that they are entitled to move the digital currency. In the end, the recipient is then granted access to ownership of such Bitcoin, and the process repeats – again proving entitlement.

Brain wallets, which have created a stir recently, is an example of this method. The concept requires a user or owner to memorize a passphrase which in turn is transformed into a 256-bit key. People warn that brain wallets are a fallible source of entropy and are not to be trusted. However, some would say this is the safest way to create and hold private keys. You are creating a number set, one seen by the public and one never seen before. The private key in its simplest form is an integer between 1 and 10^77. With this method, the uses of these mathematical relationships become infinite. A very high-powered quantum computer would have to process one trillion keys per second to crack these codes. As of right now, the most current laws of physics and the universe make it extremely difficult to process such codes.
The blockchain as a consensus-based protocol works in its functionality, as we the users take advantage of its services. As we play with Alice and Bob and the rest of the team, the consensus is based upon the network agreeing. Take for example the March 2013 hard fork, which was rejected by the miners. Meaning a whole bunch of “real” Alices and Bobs had to roll back to be accepted. In future events, the code itself and the way we play with these characters can be altered — but only as much as an open-source, peer-to-peer group of humans allow. Miners, users, developers, exchanges, and wallet servers all have a say in the current block size debate. We as a whole of individuals transacting are the blockchain. We represent the ledger by securing it with our ownership or exclusiveness to all of our keys. Both inputs and outputs are fashioned to become a system of agreements. That system is filled with Alice’s and Bob’s who are metaphors to a giant network of trust conceived by Satoshi Nakamoto.
What do you think of Alice and Bob’s role in the network? Let us know in the comments below!