A bot is a piece of malware that infects a computer to carry out commands under the remote control of the attacker.
A botnet (short for “robot network”) is a network of computers infected by malware that is under the control of a single attacking party, known as the “bot-herder.” Each machine under the control of the bot-herder is known as a bot. From one central point, the attacking party can command every computer on its botnet to simultaneously carry out coordinated criminal action. The scale of a botnet (many comprised of millions of bots) enables the attacker to perform large-scale actions previously impossible with malware. Since botnets remain under the control of a remote attacker, infected machines can receive updates and change their behavior on the fly. As a result, bot herders can often rent access to their botnet segments on the black market for significant financial gain.
Everyday botnet actions include:
- Email spam– though email is seen today as an older vector for attack, spam botnets are some of the largest. They are primarily used for sending out spam messages, often including malware, in towering numbers from each bot. The Cutwail botnet, for example, can send up to 74 billion messages daily. They are also used to spread bots to recruit more computers to the botnet.
- DDoS attacks– leverages the massive scale of the botnet to overload a target network or server with requests, rendering it inaccessible to its intended users. DDoS attacks target organizations for personal or political motives or to extort payment in exchange for ceasing the attack.
- Financial breach– includes botnets designed to steal funds from enterprises and credit card information directly. Financial botnets, like the ZeuS botnet, have been responsible for attacks involving millions of dollars stolen directly from multiple enterprises over brief periods.
- Targeted intrusions– smaller botnets designed to compromise specific high-value systems of organizations from which attackers can penetrate and intrude further into the network. These intrusions are extremely dangerous to organizations as attackers specifically target their most valuable assets, including financial data, research and development, intellectual property, and customer information.
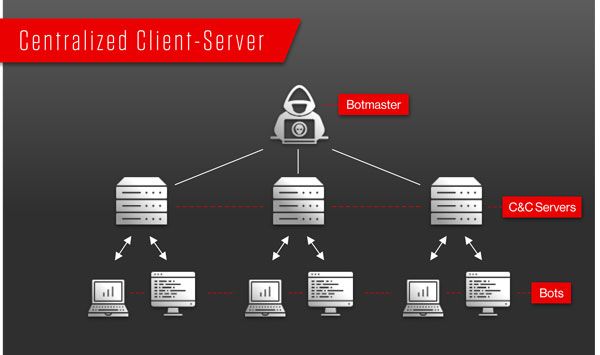
Botnets are created when the bot-herder sends the bot from his command and control servers to an unknowing recipient using file sharing, email, social media application protocols, or other bots as an intermediary. Once the recipient opens the malicious file on his computer, the bot reports to command and control, where the bot-herder can dictate commands to infected computers. Below is a diagram illustrating these relationships:

Several unique functional traits of bots and botnets make them well-suited for long-term intrusions. The bot-herder can update bots to change their entire functionality based on what he/she would like them to do and to adapt to changes and countermeasures by the target system. Bots can also utilize other infected computers on the botnet as communication channels, providing the bot-herder with a near-infinite number of communication paths to adapt to changing options and deliver updates. This highlights that infection is the most crucial step because functionality and communication methods can permanently be changed later on as needed.

As one of the most sophisticated types of modern malware, botnets are an immense cybersecurity concern to governments, enterprises, and individuals. Whereas earlier malware was a swarm of independent agents that infected and replicated themselves, botnets are centrally coordinated, networked applications that leverage networks to gain power and resilience. Since the remote bot-herder controls infected computers, a botnet is like having a malicious hacker inside your network instead of just a malicious executable program.