Over the past few years, the vulnerability of social networks like Facebook or messaging apps like Chat has given rise to using end-to-end encrypted platforms to protect communications. Today, platforms like WhatsApp, Signal, and PreVeil use end-to-end encryption to protect the exchanges of users’ data. Yet what is end-to-end encryption, and how does it work? How does it differ from other forms of data protection, and how does end-to-end encryption ensure data safety?
This piece will focus on providing answers to these questions.
- End-to-end encryption: What it is and how it works
- Can end-to-end encryption be hacked?
- Why end-to-end encryption is important and what it protects against
- What are the advantages of end-to-end encryption
- PreVeil and end-to-end encryption
End-to-end encryption: What it is and how it works
End-to-end encryption provides the gold standard for protecting communication. In an end-to-end encrypted system, the only people who can access the data are the sender, the intended recipient(s), and no one else. Neither hackers nor unwanted third parties can access the encrypted data on the server.
In true end-to-end encryption, encryption occurs at the device level. Messages and files are encrypted before they leave the phone or computer and aren’t decrypted until it reaches their destination. As a result, hackers cannot access data on the server because they do not have the private keys to decrypt the data. Instead, secret keys are stored with the individual user on their device, making accessing an individual’s data much harder.
The security behind end-to-end encryption is enabled by creating a public-private key pair. This process, also known as asymmetric cryptography, employs separate cryptographic keys for securing and decrypting the message. Public keys are widely disseminated and are used to lock or encrypt a message. Private keys are only known by the owner and are used to unlock or decrypt the message.
In end-to-end encryption, the system creates public and private cryptographic keys for each person who joins.
An example
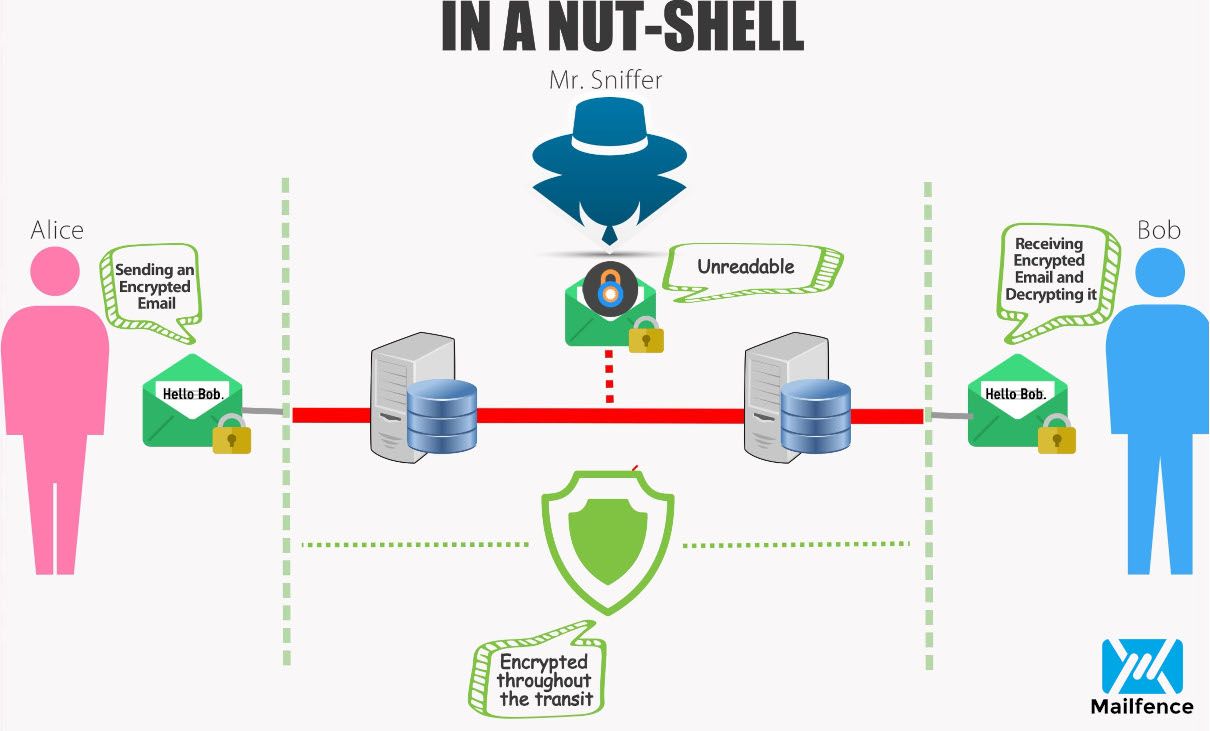
Let’s say Alice and Bob create accounts on the system. The end-to-end encrypted system provides each with a public-private key pair, whereby their public keys are stored on the server, and their private keys are stored on their device.
Alice wants to send Bob an encrypted message. She uses Bob’s public key to encrypt her message to him. Then, when Bob receives the message, he uses the private key on his device to decrypt the message from Alice.
When Bob wants to reply, he repeats the process, encrypting his message to Alice using Alice’s public key.
Can end-to-end encryption be hacked?
Security practitioners often point out that security is a chain that is only as strong as the weakest link. Bad guys will attack the weakest parts of your system because they are the parts most likely to be easily broken. Since data is most vulnerable when stored on a server, hackers’ techniques focus on gaining server access.
As the Department of Homeland Security has written:
Since attackers will go after low-hanging fruit like where the data is stored, a solution that does not protect stored data will leave information extremely vulnerable.
When practitioners use end-to-end encryption, however, the data stored on the server is encrypted; even if a hacker were to access it, all they would get is gibberish.
As the DHS goes on to state in its report:
Attacking the encrypted data is just too much work [for attackers].
Why end-to-end encryption is important and what it protects against
End-to-end encryption is necessary because it provides users and recipients security for their email and files from when the user sends the data until the recipient receives it. It also ensures that no third party can read the exchanged messages.
Services like Gmail, Yahoo, or Microsoft enable the provider to access the content of users’ data on its servers because these providers hold copies of the decryption keys. As such, these providers can read users’ emails and files. In Google’s case, its possession of decryption keys has enabled them in the past to provide the Google account holder with targeted ads.
In well-constructed end-to-end encrypted systems, the system providers never have access to the decryption keys.
What are the advantages of end-to-end encryption?
The NSA recently issued guidelines for using collaboration services. At the top of the NSA’s list was the recommendation that collaboration services employ end-to-end encryption. End-to-end’s inclusion in the NSA’s list highlights its shift to the mainstream by an organization known to seek the highest levels of security for themselves and their technologies. The NSA notes that users can reduce their risk exposure and become more challenging targets for bad actors by following the guidelines it defines.
The advantages of end-to-end encryption Ensures your data is secure from hacks: With end to end encryption, you are the only one who has the private key to unlock your data. Data on the server can’t be read by hackers because they do not have the private keys to decrypt the information. Protects your privacy: Providers like Google and Microsoft can read your data. When you use their service, data is decrypted on their servers. If data is decrypted on their servers, then hackers and unwanted third parties can read it, too. Protects admins: Since admins don’t hold the decryption keys to decrypt the data, any attack that targets administrators will come up short.
The U.S. State Department has also wised up to the benefits of end-to-end encryption with their ITAR Carve out for Encrypted Technical data. The carve-out establishes that defense companies can now share unclassified technical data outside the U.S. with authorized persons. This exchange can be done without requiring an export license so long as the data is adequately secured with end-to-end encryption. If the data is end-to-end encrypted, the exchange is not considered an export.
The NSA’s and State Department’s statements acknowledge that end-to-end encryption provides a significant advantage to users over traditional forms of encryption. End-to-end encryption secures data on the user’s device and only decrypts it on the recipient’s device. This means the data can never be decrypted on the server, in transit, or on the user’s device.