Like a regular system holder, you might wonder why your system is running slower than usual. You are always getting random messages like pop-ups, something got added as an extension in your browser, and you have never used this. Your browser cannot load the page, internet connectivity is slow, and even the computer is always slow, and sometimes it even crashes. We have no idea why all this is happening.
Well, the only answer is malware which is doing all such things. Your machine has been infected awfully, and it can only become proper by turning into a zombie, which C&C controls.
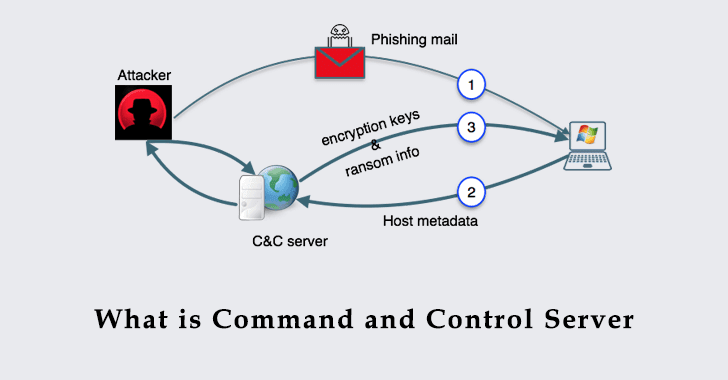
You might be wondering what is all about C&C? This full name is Command-and-control servers. The hackers mainly use the system to communicate with a target network. These systems may be Smartphones, Computers, loT’s, etc.
Just in the second paragraph, we have mentioned the name called “zombie,” which is also called a botnet that is a combination of robot and network. This machine is infected with the Trojan horse, which gets controlled by the C2C server. This botnet is the collection of computer sets that get used without their owners’ knowledge and sends files to other computers through the internet. The file includes spam and malware.
Now the question is why communication is required? Well, the answer is botnets has to follow the instruction given by C&C. The instruction has set as command-based, which is the structure of the botnet. It has been installed as a key logger which can collect sensitive information like spam emails, credit card numbers, conduct DDoS attacks, etc. The botnet cannot upload the reports or give them the result because it can only do whatever the commander (C&C) tells them.
What can hackers do through Command and Control?
- Data theft: In this process, a company’s data which is very sensitive, like financial documents, can be copied, and those also can be transferred to the attacker’s server.
- Shutdown: One attacker can shut down many machines together and even make the network slow of the targeted company.
- Reboot: When the computer gets infected, it may suddenly shut down and reboot, becoming a problem for any regular business operation.
- Distributed denial of service (DDoS): It overwhelms the server and floods them with too much internet traffic. As soon as the botnet gets established attacker will instruct every bot to send a request to the company’s targeted IP address. This creates an appeal with the targeted server, and traffic gets clogged on the highway. It can legitimate the traffic by attacking IP addresses, and it denies access—this type of attack they do to make the website down.
This is the diagram where you can see how to stop the attacker from using DNS against you:


While reading this article, you might wonder why we need bots and what their uses are. Let us take an example of spamming. Sending spam is getting blacklisted because it is already set in some specific address. To overcome this issue, you need to send spam, but for zombies to find the unique address from thousands, it is a cupcake for it. By sending more emails, attackers can make enormous money.
If you consider that the C&C server is intended to conduct DDoS, then Zoobies’s army keeps sending the false request to the web server, and the webserver will not be able to handle the multiple request time. They will make the leading attack on DDoS. After this, criminals want money, and they demand from the owner, and after getting that, they will stop such an attack.
It is effortless for a botnet to create a zombie army by installing software by stealing a password. This software mainly steals passwords from bank accounts, emails, credit card numbers, and criminals who sell passwords to make money. Zombie army only deals with all illegal activity.
Botnet Architecture Types
There are two types of architecture which include centralized and decentralized or peer-to-peer. These are discussed below:
- Centralized: This is a prevalent type centralized with a C&C server, which provides the resources by individual client request. This network is wholly based on the client-server model. Usually, this type of botnet gets to communicate via internet relay chat (IRC).
- IRC is a computer program that users can easily install in their system.
- Clients can send transfer messages to the other client through the chat server.
- IRC is not so simple, and it uses the low bandwidth communication method, which makes them a broader use to host botnets.
- They look straightforward for the construction, and it gets used to getting moderate success so that they can coordinate with DDoS attacks and switch the channel to avoid them.
- Decentralized or Peer-to-Peer: Desperately using centralized servers has its advantage. There is a problem with using centralized servers if IRC uses that. Botnet clients must know about the IRC server, port, and other channels. To halt the botnet attack, anti-malware organizations detect the server and make it shut down. To bring down a centralized server, you must leave the zombies dead, and the botnet army will not work with the attackers.
The Overview of Infection Methods:
You might wonder how C&C recruitment has been done and how to create an army for botnets. Let us inform you there are multiple ways to turn the computer into a botnet. Those are discussed below:
- Email: Usually, attackers send you an email with a code in an attached file, or sometimes they even send a link with malicious code. After clicking on the link will lure the attacker, which drops the malware within the machine, and it will turn into a Zombie.
- Exploiting Vulnerabilities: Many vulnerabilities get exploited, offered from the backdoor of the machine. This mainly gets used by the attacker, who drops the malware into the machine. Vulnerabilities include browser plugins, add-ons, and other software installed on the device.
What will you do when the computer turns into Zombie?
- You can use some Sysinternals tools to find the process to consume more memory. If it finds any suspicious process, then you can kill that process.
- You always need to scan the machine with a different antivirus engine to recheck whether it is getting detected or not malware. This cannot be the complete solution, but it has to identify the malware with the latest signature.
- Leading antivirus fails to detect and remove the malware if it’s the most advanced. It can link itself with the operating system and process.
- If the rootkit is complicated and cannot remove the infection, the most effective thing is to clean the machine and restoring the backup. But before you start, make sure that you keep a backup of everything, so you do not lose any data.
- After you clean the malware, you can regularly apply the security update to avoid future infection.
Conclusion
By reading this article, you have learned how much C2 is essential for our daily life. Just a tiny malware can do massive damage, so we have taken the help of a botnet army that can control everything and communicate better.