DNS was not designed with security in mind, and many types of attacks were created to exploit vulnerabilities in the DNS system.
What is DNS security?
DNS security protects DNS infrastructure from cyber attacks to keep it performing quickly and reliably. An effective DNS security strategy incorporates several overlapping defenses, including establishing redundant DNS servers, applying security protocols like DNSSEC, and requiring rigorous DNS logging.
Why is DNS security important?
Like many Internet protocols, the DNS system was not designed with security in mind and contained several design limitations. These limitations and technological advances make DNS servers vulnerable to various attacks, including spoofing, amplification, DoS (Denial of Service), or the interception of private personal information. And since DNS is an integral part of most Internet requests, it can be a prime attack target.
In addition, DNS attacks are frequently deployed in conjunction with other cyberattacks to distract security teams from the actual target. An organization must quickly mitigate DNS attacks so they are not too busy to handle simultaneous attacks through other vectors.
What are some common DNS attacks?
Attackers have found several ways to target and exploit DNS servers. Here are some of the most common DNS attacks:
DNS spoofing/cache poisoning: This is an attack where forged DNS data is introduced into a DNS resolver’s cache, resulting in the resolver returning an incorrect IP address for a domain. Instead of going to the correct website, traffic can be diverted to a malicious machine or anywhere else the attacker desires; often, this will be a replica of the original site used for malicious purposes such as distributing malware or collecting login information.
DNS tunneling: This attack uses other protocols to tunnel through DNS queries and responses. Attackers can use SSH, TCP, or HTTP to pass malware or stolen information into DNS queries, undetected by most firewalls.
DNS hijacking: The attacker redirects queries to a different domain name server in DNS hijacking. This can be done either with malware or with the unauthorized modification of a DNS server. Although the result is similar to that of DNS spoofing, this is a fundamentally different attack because it targets the DNS record of the website on the nameserver, rather than a resolver’s cache.
NXDOMAIN attack: This is a type of DNS flood attack where an attacker inundates a DNS server with requests, asking for records that do not exist, in an attempt to cause a denial of service for legitimate traffic. This can be accomplished using sophisticated attack tools that auto-generate unique subdomains for each request. NXDOMAIN attacks can also target a recursive resolver to fill the resolver’s cache with junk requests.
Phantom domain attack: A phantom domain attack has a similar result to an NXDOMAIN attack on a DNS resolver. The attacker sets up a bunch of ‘phantom’ domain servers that either respond to requests very slowly or not at all. The resolver is then hit with a flood of requests to these domains and gets tied up waiting for responses, leading to slow performance and denial of service.
Random subdomain attack: In this case, the attacker sends DNS queries for several random, nonexistent subdomains of one legitimate site. The goal is to create a denial-of-service for the domain’s authoritative nameserver, making it impossible to look up the website from the nameserver. As a side effect, the ISP serving the attacker may also be impacted, as their recursive resolver’s cache will be loaded with evil requests.
Domain lock-up attack: Attackers orchestrate this attack by setting up particular domains and resolvers to create TCP connections with other legitimate resolvers. When the targeted resolvers send requests, these domains send back slow streams of random packets, tying up the resolver’s resources.
Botnet-based CPE attack: These attacks are carried out using CPE devices (Customer Premise Equipment; this is hardware given out by service providers for use by their customers, such as modems, routers, cable boxes, etc.). The attackers compromise the CPEs and the devices become part of a botnet, used to perform random subdomain attacks against one site or domain.
What is DNSSEC?
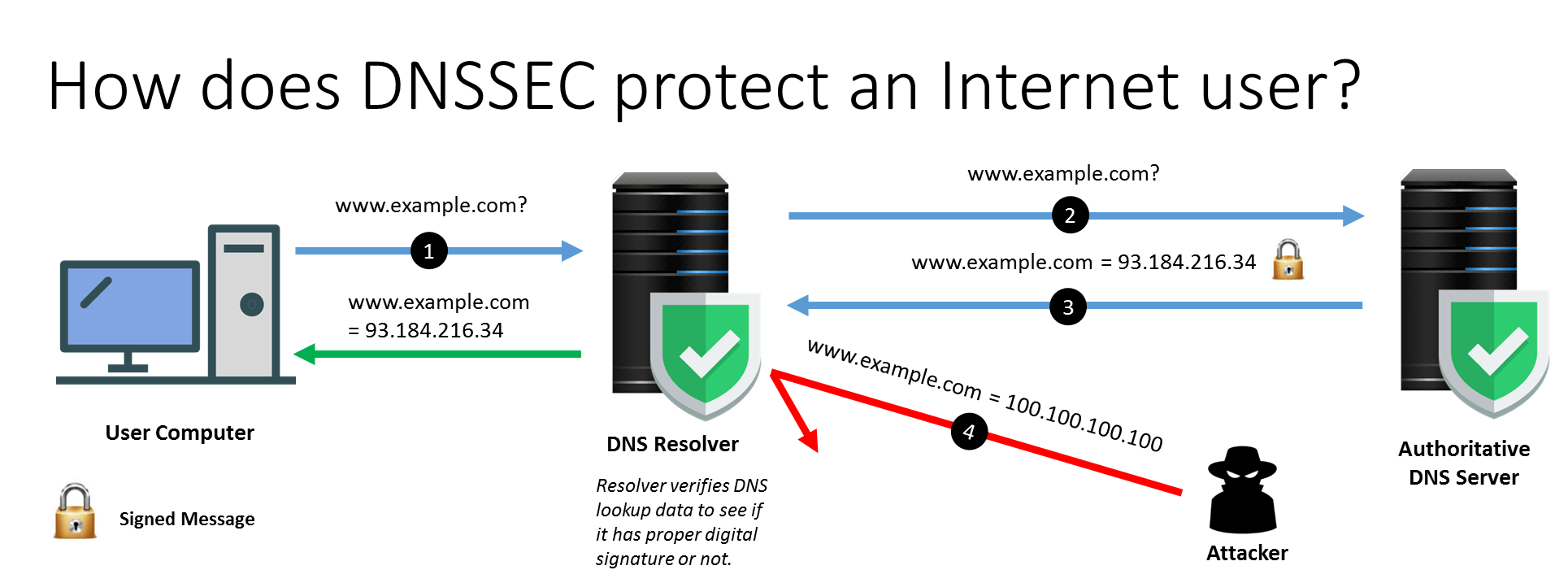
DNS Security Extensions (DNSSEC) is a security protocol created to mitigate this problem. DNSSEC protects against attacks by digitally signing data to help ensure its validity. The signing must happen at every level in the DNS lookup process to ensure a secure lookup.
This signing process is similar to someone signing a legal document with a pen; that person signs with a unique signature that no one else can create, and a court expert can look at that signature and verify that that person signed the document. These digital signatures ensure that data has not been tampered with.
DNSSEC implements a hierarchical digital signing policy across all layers of DNS. For example, in the case of a ‘google.com’ lookup, a root DNS server would sign a key for the .COM nameserver, and the.COM nameserver would then sign a key for google.com’s authoritative nameserver.
While improved security is always preferred, DNSSEC is designed to be backward-compatible to ensure that traditional DNS lookups resolve correctly, albeit without the added security. DNSSEC is meant to work with other security measures like SSL/TLS as part of a holistic Internet security strategy.
DNSSEC creates a parent-child train of trust that travels up to the root zone. This chain of trust cannot be compromised at any layer of DNS, or the request will become open to an on-path attack.
To close the chain of trust, the root zone itself needs to be validated (proven free of tampering or fraud), which is done using human intervention. Interestingly, in a Root Zone Signing Ceremony, selected individuals worldwide meet to sign the root DNSKEY RRset in a public and audited way.
What are other ways of protecting against DNS-based attacks?
In addition to DNSSEC, an operator of a DNS zone can take further measures to secure their servers. Over-provisioning infrastructure is a straightforward strategy to overcome DDoS attacks. If your nameservers can handle several multiples more traffic than expected, it is harder for a volume-based attack to overwhelm your server. Organizations can accomplish this by increasing their DNS server’s total traffic capacity, establishing multiple redundant DNS servers, and using load balancing to route DNS requests to healthy servers when one begins to perform poorly.
Another strategy still is a DNS firewall.
What is a DNS firewall?
A DNS firewall is a tool that can provide several security and performance services for DNS servers. A DNS firewall sits between a user’s recursive resolver and the authoritative nameserver of the website or service they are trying to reach. The firewall can provide rate-limiting services to shut down attackers trying to overwhelm the server. Suppose the server does experience downtime due to an attack or for any other reason. In that case, the DNS firewall can keep the operator’s site or service up by serving DNS responses from the cache.
In addition to its security features, a DNS firewall can provide performance solutions such as faster DNS lookups and reduced bandwidth costs for the DNS operator.
DNS as a security tool
DNS resolvers can also be configured to provide security solutions for their end users (people browsing the Internet). Some DNS resolvers provide features such as content filtering, which can block sites known to distribute malware and spam, and botnet protection, which blocks communication with known botnets. Many of these secured DNS resolvers are free to use and a user can switch to one of these recursive DNS services by changing a single setting in their local router.
Are DNS queries private?
Another important DNS security issue is user privacy. DNS queries are not encrypted. Even if users use a DNS resolver like 1.1.1.1 that does not track their activities, DNS queries travel over the Internet in plaintext. Anyone who intercepts the query can see which websites the user is visiting.
This lack of privacy impacts security and, in some cases, human rights; if DNS queries are not private, it becomes easier for governments to censor the Internet and for attackers to stalk users’ online behavior.
DNS over TLS and DNS over HTTPS are two standards for encrypting DNS queries to prevent external parties from being able to read them.