Zero Trust is a security model based on maintaining strict access controls and not trusting anyone by default, even those already inside the network perimeter.
What is Zero Trust security?
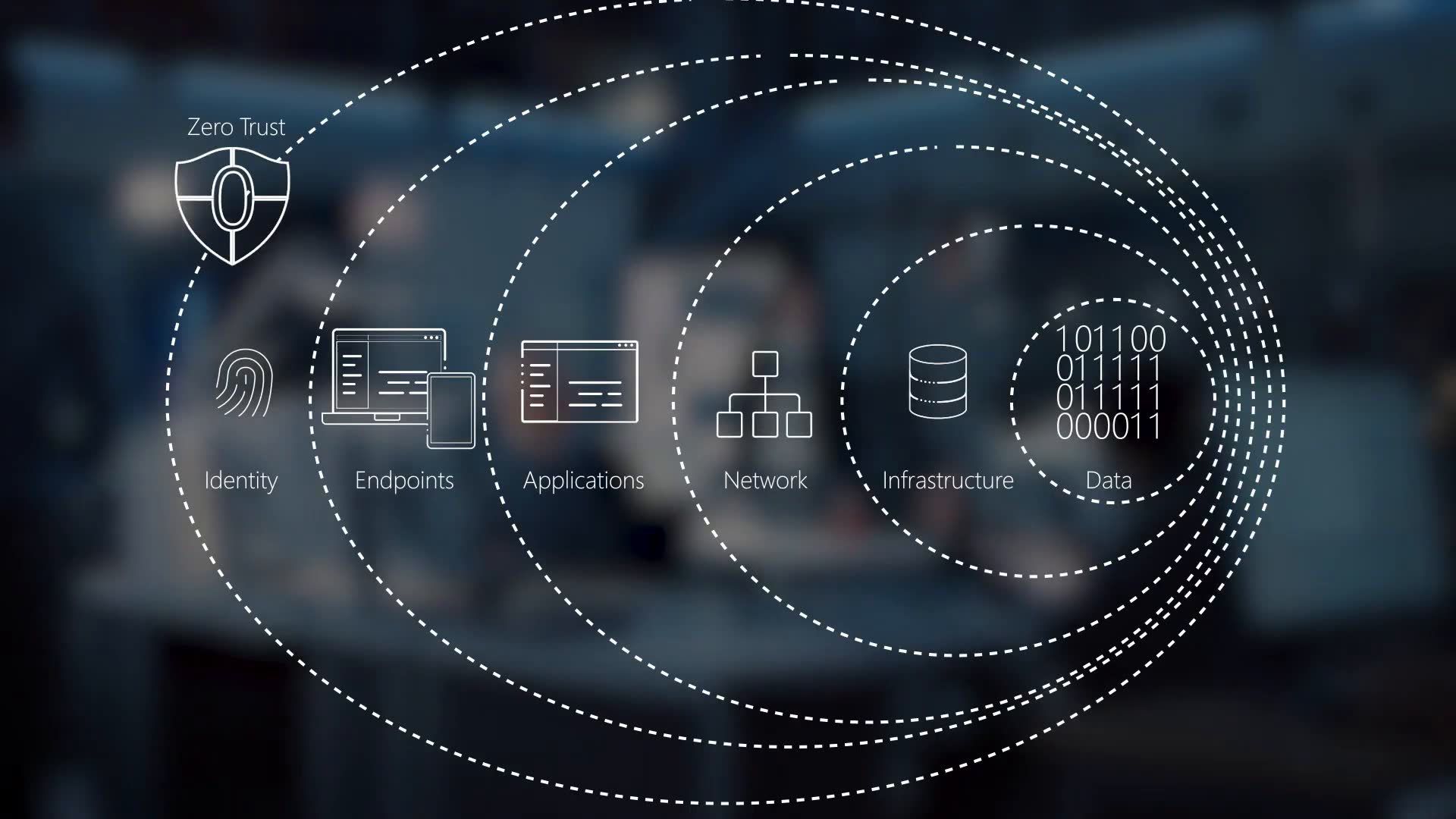
Zero Trust security is an IT security model that requires strict identity verification for every person and device trying to access resources on a private network, regardless of whether they are sitting within or outside the network perimeter. ZTNA is the main technology associated with Zero Trust architecture. Still, Zero Trust is a holistic approach to network security that incorporates several different principles and technologies.
More simply put: traditional IT network security trusts anyone and anything inside the network. A Zero Trust architecture trusts no one and nothing.
Traditional IT network security is based on the castle-and-moat concept. In castle-and-moat security, obtaining access from outside the network is hard, but everyone inside the network is trusted by default. The problem with this approach is that once an attacker gains access to the network, they have free rein over everything inside.

This vulnerability in castle-and-moat security systems is exacerbated by companies no longer having their data in just one place. Today, information is often spread across cloud vendors, which makes it more challenging to have a single security control for an entire network.
Zero Trust security means that no one is trusted by default from inside or outside the network, and verification is required from everyone trying to gain access to resources on the network. This added layer of security has been shown to prevent data breaches. Studies have shown that the average cost of a single data breach is over $3 million. Considering that figure, it should be no surprise that many organizations are eager to adopt a Zero Trust security policy.
What are the main principles behind Zero Trust?
Continuous monitoring and validation
The philosophy behind a Zero Trust network assumes that there are attackers within and outside the network, so no users or machines should be automatically trusted. Zero Trust verifies user identity, privileges, device identity, and security. Logins and connections time out periodically once established, forcing users and devices to be continuously re-verified.
Least privilege
Another principle of zero trust security is least privilege access. This means giving users only as much access as they need, like an army general giving soldiers information on a need-to-know basis. This minimizes each user’s exposure to sensitive parts of the network.
Implementing the least privilege involves careful management of user permissions. VPNs are not well-suited for least-privilege approaches to authorization, as logging in to a VPN gives a user access to the whole connected network.
Device access control
In addition to controls on user access, Zero Trust also requires strict controls on device access. Zero Trust systems need to monitor how many different devices are trying to access their network, ensure that every device is authorized, and assess all devices to ensure they have not been compromised. This further minimizes the attack surface of the network.
Microsegmentation
Zero Trust networks also utilize micro-segmentation. Microsegmentation is breaking up security perimeters into small zones to maintain access to separate network parts. For example, a network with files in a single data center that utilizes micro-segmentation may contain dozens of separate, secure zones. A person or program with access to one of those zones will not be able to access any of the other zones without separate authorization.
Preventing lateral movement
In network security, “lateral movement” is when an attacker moves within a network after gaining access. Lateral movement can be difficult to detect even if the attacker’s entry point is discovered because the attacker will have gone on to compromise other parts of the network.
Zero Trust is designed to contain attackers so they cannot move laterally. Because Zero Trust access is segmented and has to be re-established periodically, an attacker cannot move across to other microsegments within the network. Once the attacker’s presence is detected, the compromised device or user account can be quarantined and removed from further access. (In a castle-and-moat model, if lateral movement is possible for the attacker, quarantining the original compromised device or user has little to no effect since the attacker already has reached other parts of the network.)
Multi-factor authentication (MFA)
Multi-factor authentication (MFA) is also a Zero Trust security core value. MFA requires more than one piece of evidence to authenticate a user; just entering a password is not enough to gain access. A commonly seen application of MFA is the 2-factor authorization (2FA) used on online platforms like Facebook and Google. In addition to entering a password, users who enable 2FA for these services must also enter a code sent to another device, such as a mobile phone, thus providing two pieces of evidence that they are who they claim to be.
What are the benefits of Zero Trust?
Zero Trust as a philosophy is better suited to modern IT environments than more traditional security approaches. With such a wide variety of users and devices accessing internal data and data stored inside and outside the network (in the cloud), it is far safer to assume that no user or device is trustworthy than to presume that preventative security measures have plugged all the holes.
The primary benefit of applying Zero Trust principles is to help reduce an organization’s attack surface. Additionally, Zero Trust minimizes the damage when an attack occurs by restricting the breach to a tiny area via micro-segmentation, lowering the recovery cost. Zero Trust reduces the impact of user credential theft and phishing attacks by requiring multiple authentication factors. It helps eliminate threats that bypass traditional perimeter-oriented protections.
By verifying every request, Zero Trust security reduces the risk posed by vulnerable devices, including IoT devices, which are often difficult to secure and update (see IoT security).
What is the history of Zero Trust security?
The term “Zero Trust” was coined by an analyst at Forrester Research Inc. in 2010 when the model for the concept was first presented. A few years later, Google announced that they had implemented Zero Trust security in their network, which led to a growing interest in adoption within the tech community. In 2019, Gartner, a global research and advisory firm, listed Zero Trust security access as a core component of secure access service edge (SASE) solutions.
What is Zero Trust Network Access (ZTNA)?
Zero Trust Network Access (ZTNA) is the main technology that enables organizations to implement Zero Trust security. Like a software-defined perimeter (SDP), ZTNA conceals most infrastructure and services, setting up one-to-one encrypted connections between devices and the necessary resources.
What are some Zero Trust use cases?
Any organization that relies on a network and stores digital data will probably consider using a zero-trust architecture. But some of the most common use cases for Zero Trust include:
Replacing or augmenting a VPN: Many organizations rely on VPNs to protect their data, but as described above, VPNs are often not ideal for defending against today’s risks.
Securely supporting remote work: While VPNs create bottlenecks and can slow productivity for remote workers, Zero Trust can extend secure access control to connections from anywhere.
Access control for cloud and multi-cloud: A Zero Trust network verifies any request, regardless of source or destination. It can also help reduce unauthorized cloud-based services (called “shadow IT”) by controlling or blocking unsanctioned apps.
Onboarding third parties and contractors: Zero Trust can quickly extend restricted, least-privilege access to external parties, who typically use computers not managed by internal IT teams.
Rapidly onboarding new employees: Zero Trust networks can also facilitate quickly onboarding new internal users, making them a good fit for fast-growing organizations. In contrast, a VPN may need more capacity to accommodate many new users.
What are the leading Zero Trust best practices?
- Monitor network traffic and connected devices: Visibility is crucial for users and machines to be verified and authenticated.
- Keep devices updated: Vulnerabilities need to be patched as quickly as possible. Zero Trust networks should be able to restrict access to vulnerable devices (another reason why monitoring and validation are key).
- Apply the principle of least privilege for everyone in the organization: Everyone from executives to IT teams should have the least access they need. This minimizes the damage if an end-user account becomes compromised.
- Partition the network: Breaking the network into smaller chunks helps ensure breaches are contained early before they can spread. Microsegmentation is an effective way to do this.
- Act as if the network perimeter did not exist: Unless a network is entirely air-gapped (a rarity), the points where it touches the Internet or the cloud are probably too numerous to eliminate.
- Use security keys for MFA: Hardware-based security tokens are more secure than soft tokens like one-time passcodes (OTPs) sent via SMS or email.
- Incorporate threat intelligence: Since attackers are constantly updating and refining their tactics, subscribing to the latest threat intelligence data feeds is critical for identifying threats before they spread.
- Avoid motivating end users to circumvent security measures: Just as overly strict password requirements incentivize users to recycle the same passwords repeatedly, forcing users to re-authenticate once an hour via multiple identity factors may be too much, ironically decreasing security. Always keep the end user’s needs in mind.