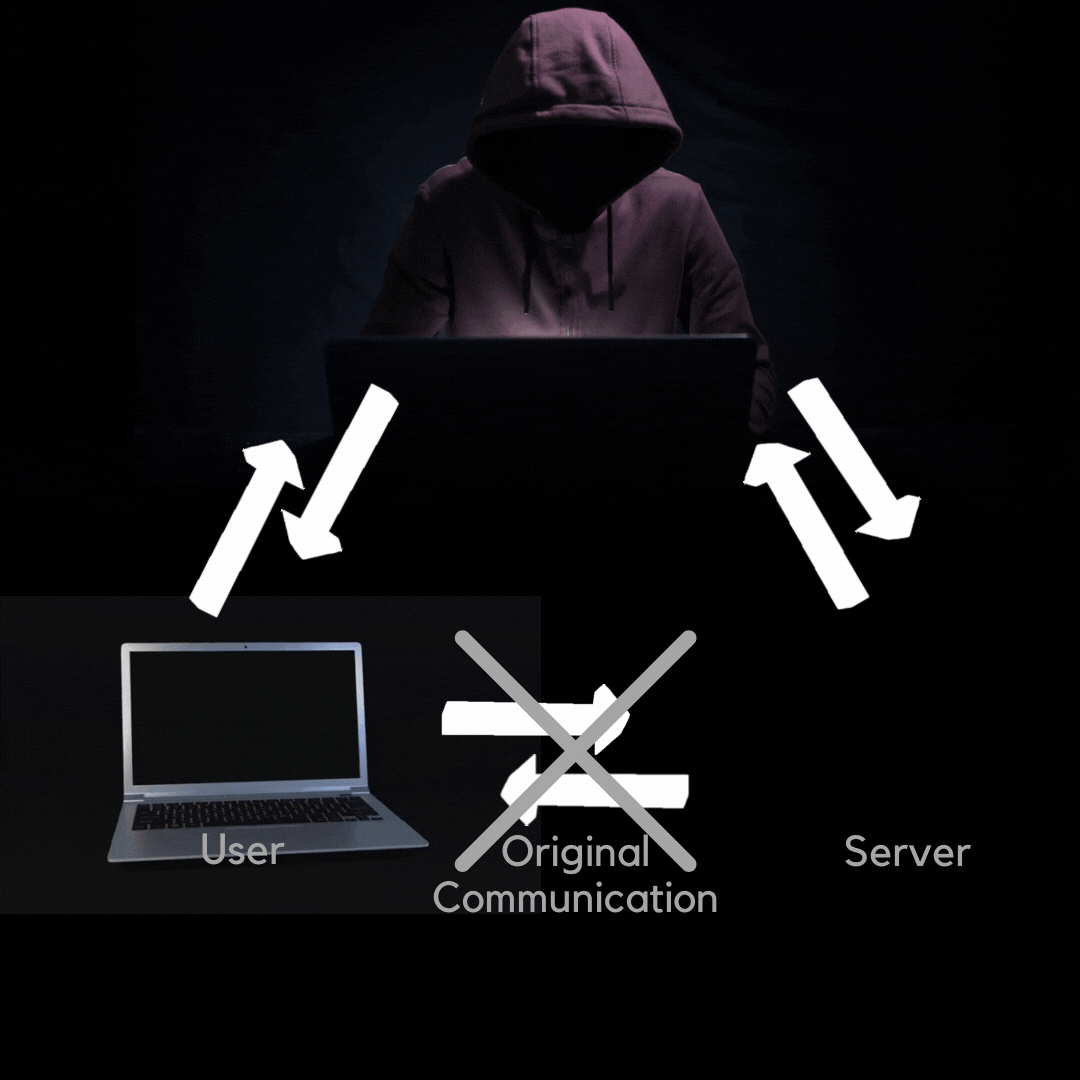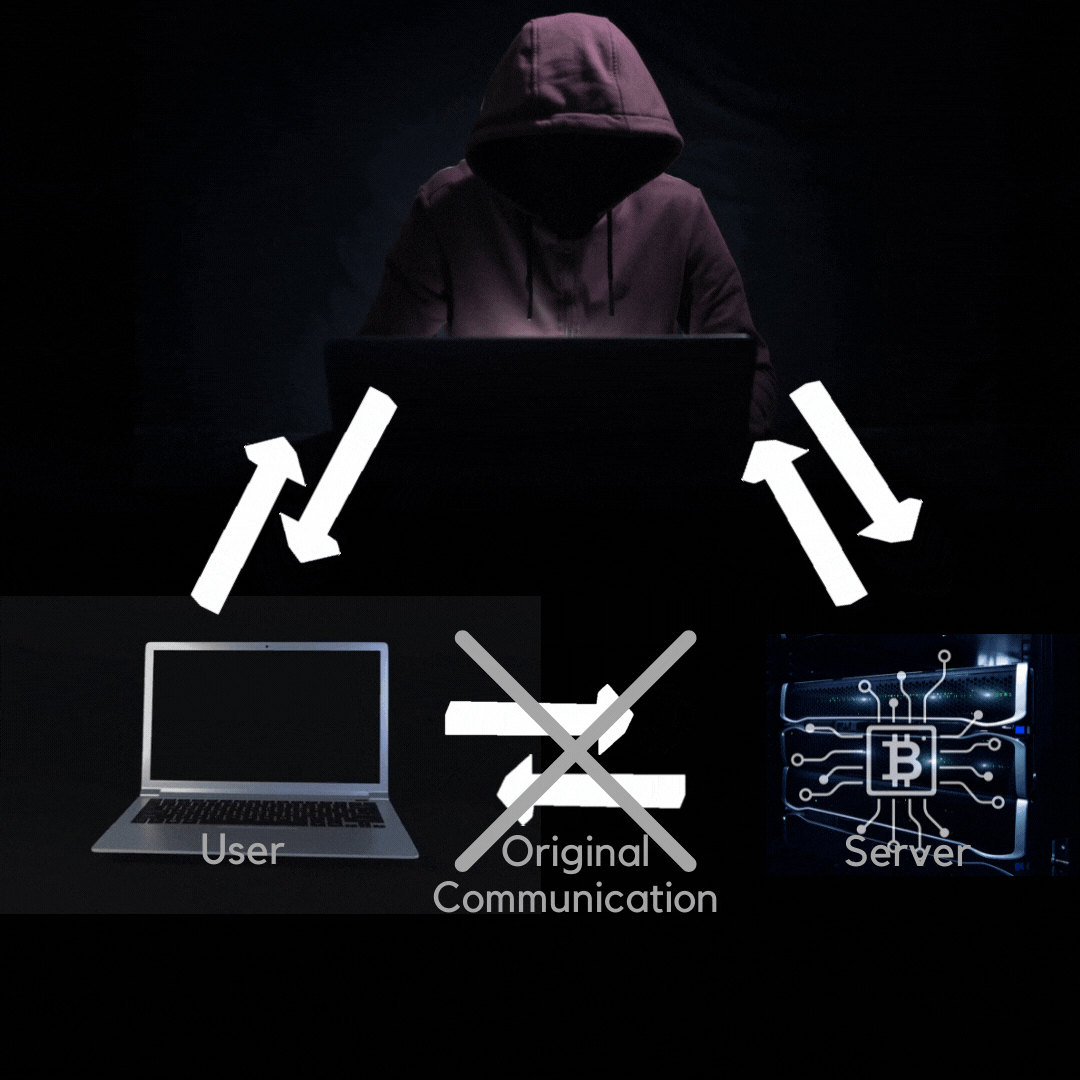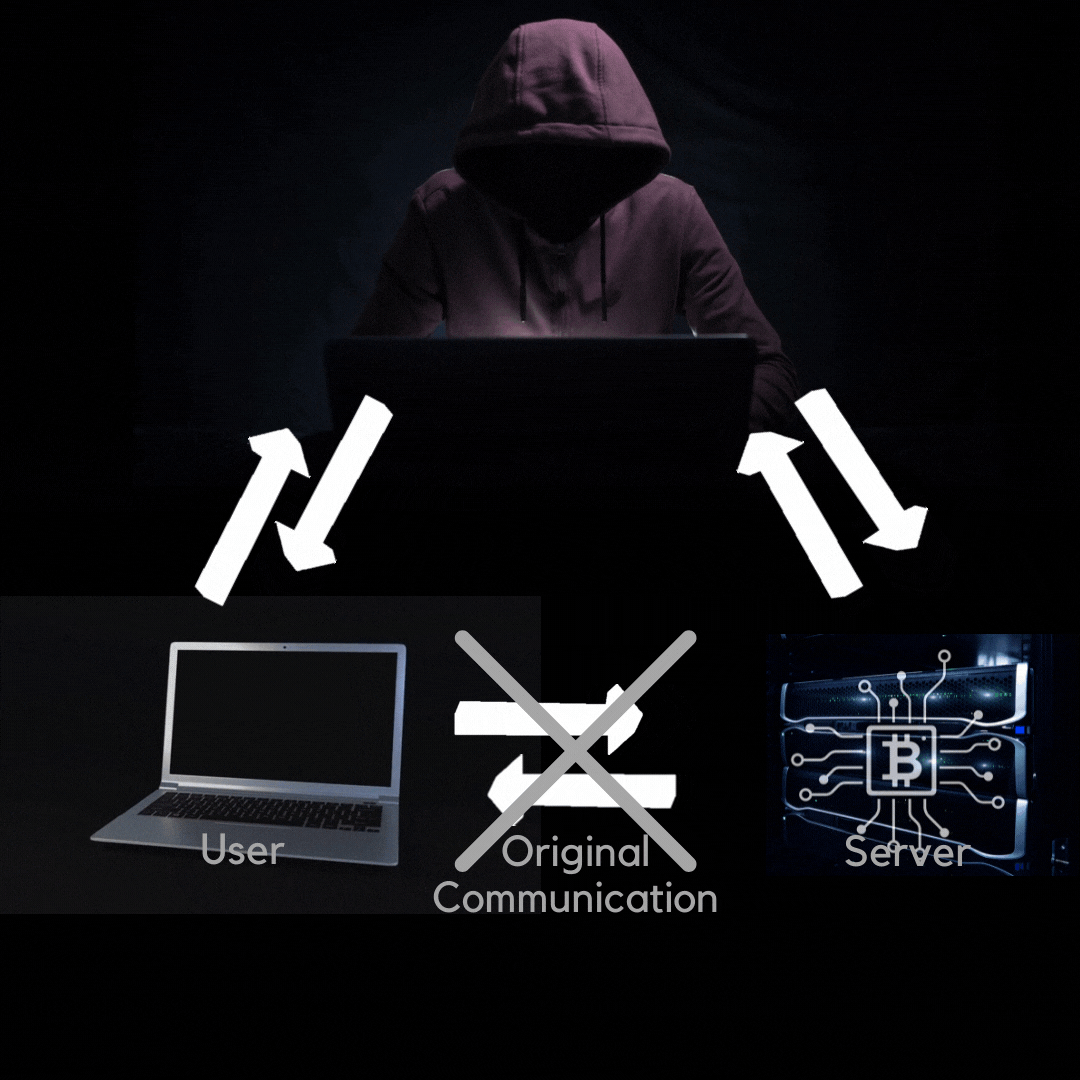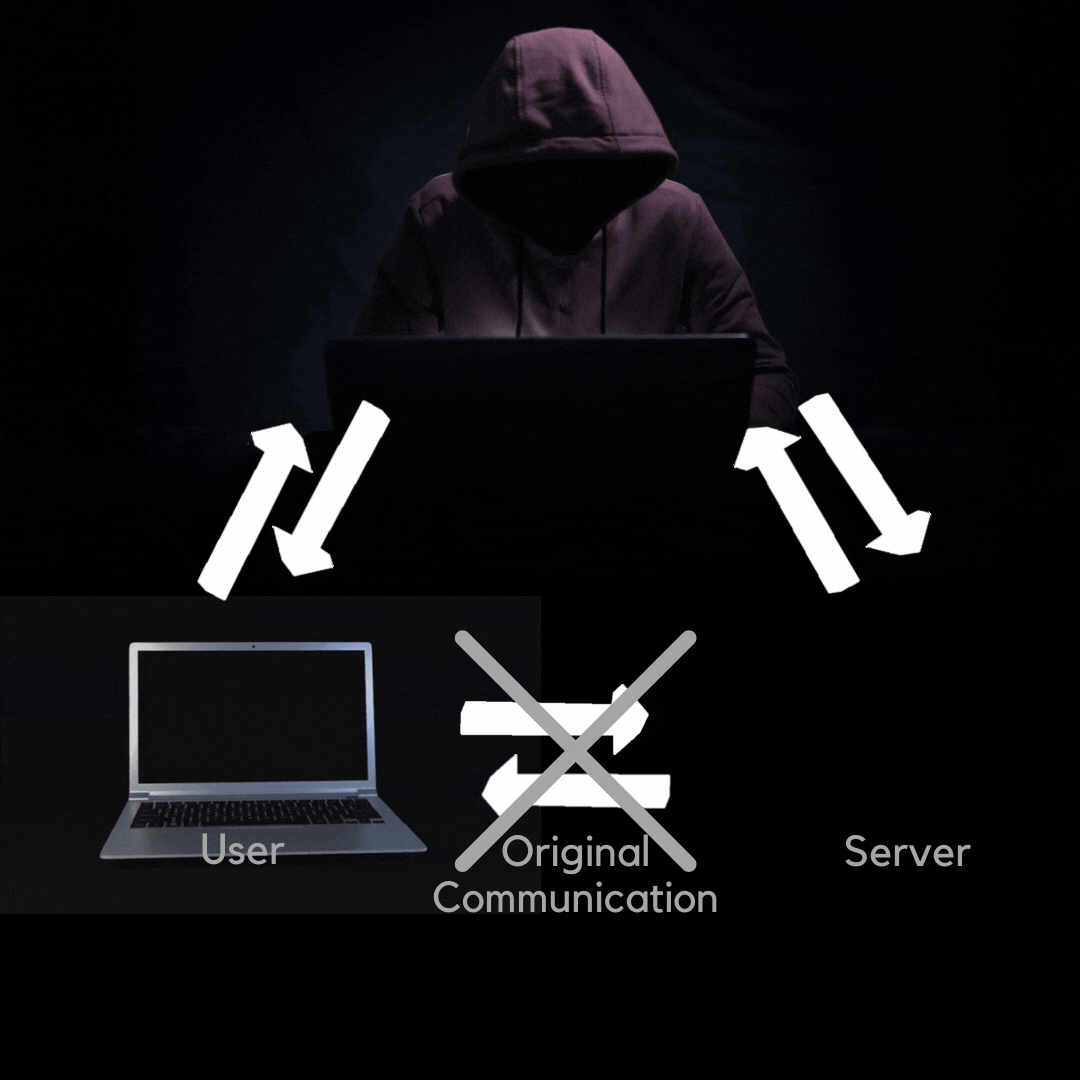
An on-path attacker places themselves between victims and the services they are trying to reach, often to steal data.
On-path attackers place themselves between two devices (often a web browser and a web server) and intercept or modify communications. The attackers can then collect information and impersonate either of the two agents. In addition to websites, these attacks can target email communications, DNS lookups, and public WiFi networks. Typical targets of on-path attackers include SaaS businesses, e-commerce businesses, and users of financial apps.
You can think of an on-path attacker like a rogue postal worker sitting in a post office and intercepting letters between two people. This postal worker can read private messages and even edit the contents of those letters before passing them along to their intended recipients.
In a more modern example, an on-path attacker can sit between a user and the website they want to visit and collect their username and password. This can be done by targeting the HTTP connection between the user and the website; hijacking this connection lets an attacker act as a proxy, collecting and modifying information sent between the user and the site. Alternatively, the attacker can steal a user’s cookies (small pieces of data created by a website and stored on a user’s computer for identification and other purposes). These stolen cookies can hijack a user’s session, letting an attacker impersonate that user on the site.
On-path attackers can also target DNS servers. The DNS lookup process allows web browsers to find websites by translating domain names into IP addresses. In DNS on-path attacks such as DNS spoofing and DNS hijacking, an attacker can compromise the DNS lookup process and send users to the wrong sites. These sites often distribute malware and/or collect sensitive information.
What is email hijacking?
Another joint attack is email hijacking, which on-path attackers use to infiltrate email servers by putting themselves between an email server and the web. Once the server is compromised, the attackers can monitor email communications for various purposes. One such scam involves waiting for a scenario where one person needs to transfer money to another (e.g., a customer paying a business). The attackers can then use a spoofed email address to request that the money be transferred to an attacker’s account. The email will seem legitimate and innocuous to the recipient (“Sorry, there’s a typo in my last email! My account number is actually: XXX-XXXX”), making this attack very practical and financially devastating. In 2015, a cybercrime ring in Belgium used email hijacking to steal over 6 million euro from various European companies.
Why is it risky to use public WiFi networks?
On-path attacks are frequently perpetrated over WiFi networks. Attackers can create malicious WiFi networks that seem harmless or clones of legitimate WiFi networks. Once a user connects to the compromised WiFi network, an on-path attacker can monitor that user’s online activity. Sophisticated attackers may even redirect the user’s browser to fake copies of legitimate websites.
What are ways to protect against on-path attackers?
Since on-path attackers use several methods, there is no all-in-one solution for these attacks. One of the most fundamental ways to protect against attacks that target HTTP traffic is to adopt SSL/TLS, which creates secure connections between users and web services. Unfortunately, this is not a foolproof solution, as more sophisticated on-path attackers can work around SSL/TLS protection. To further protect against these attacks, some web services implement HTTP Strict Transport Security (HSTS), which forces secure SSL/TLS connections with any browser or app, blocking unsecured HTTP connections and preventing cookie theft.
Authentication certificates can also be used to protect against these attacks. An organization can implement certificate-based authentication on all their devices so that only users with adequately configured certificates can access their system.
Secure/Multipurpose Internet Mail Extensions (S/MIME) can be used to prevent email hijacking. This protocol encrypts emails and lets users digitally sign emails with a unique Digital Certificate, letting the receiver know the message is legitimate.
Individual users can also protect themselves from on-path attackers by avoiding submitting sensitive information on any public WiFi network unless protected by a secure Virtual Private Network (VPN).