In a TLS/SSL handshake, clients and servers exchange SSL certificates, cipher suite requirements, and randomly generated data for creating session keys.
TLS is an encryption and authentication protocol designed to secure Internet communications. A TLS handshake is the process that kicks off a communication session that uses TLS. During a TLS handshake, the two communicating sides exchange messages to acknowledge each other, verify each other, establish the cryptographic algorithms they will use, and agree on session keys. TLS handshakes are a foundational part of how HTTPS works.
TLS vs. SSL handshakes
SSL, or Secure Sockets Layer, was the original security protocol developed for HTTP. Some time ago, SSL was replaced by TLS or Transport Layer Security. SSL handshakes are now called TLS handshakes, although the “SSL” name is still widely used.
When does a TLS handshake occur?
A TLS handshake occurs whenever a user navigates to a website over HTTPS, and the browser begins to query the website’s origin server. A TLS handshake happens whenever other communications use HTTPS, including API calls and DNS over HTTPS queries.
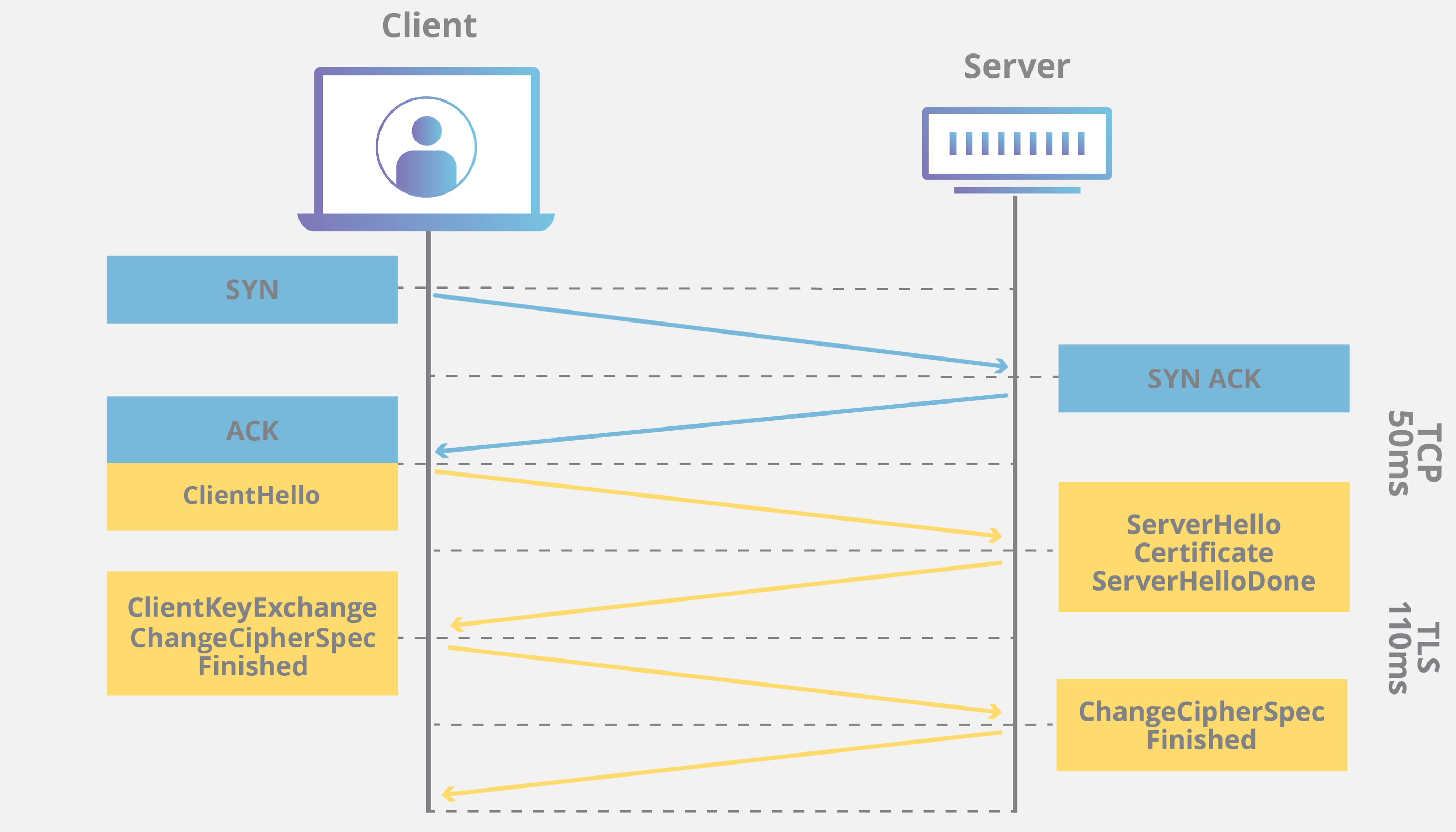
TLS handshakes occur after a TCP connection has been opened via a TCP handshake.
What happens during a TLS handshake?
During a TLS handshake, the client and server together will do the following:
- Specify which version of TLS (TLS 1.0, 1.2, 1.3, etc.) they will use
- Decide on which cipher suites (see below) they will use
- Authenticate the identity of the server via the server’s public key and the SSL certificate authority’s digital signature
- Generate session keys to use symmetric encryption after the handshake is complete
What are the steps of a TLS handshake?
TLS handshakes are a series of datagrams, or messages, by a client and a server. A TLS handshake involves multiple steps, as the client and server exchange the information necessary for completing the handshake and making further conversation possible.
The exact steps within a TLS handshake will vary depending upon the kind of key exchange algorithm used and the cipher suites supported by both sides. While now considered not secure, the RSA key exchange algorithm was used in TLS versions before 1.3. It goes roughly as follows:
- The ‘client hello’ message initiates the handshake by sending a “hello” message to the server. The message will include which TLS version the client supports, the cipher suites supported, and a string of random bytes known as the “client random.”
- The ‘server hello’ message: In reply to the client hello message, the server sends a message containing the server’s SSL certificate, the server’s chosen cipher suite, and the “server random,” another random string of bytes generated by the server.
- Authentication: The client verifies the server’s SSL certificate with the certificate authority that issued it. This confirms that the server is who it says it is, and that the client is interacting with the actual owner of the domain.
- The premaster secret: The client sends one more random string of bytes, the “premaster secret.” The premaster secret is encrypted with the public key and can only be decrypted with the private key by the server. (The client gets the public key from the server’s SSL certificate.)
- The private key used: The server decrypts the premaster secret.
- Session keys created: Both client and server generate session keys from the client random, the server random, and the premaster secret. They should arrive at the same results.
- The client is ready: The client sends a “finished” message encrypted with a session key.
- The server is ready: The server sends a “finished” message encrypted with a session key.
- Secure symmetric encryption achieved: The handshake is completed, and communication continues using the session keys.
All TLS handshakes make use of asymmetric cryptography (the public and private key), but not all will use the private key in the process of generating session keys. For instance, an ephemeral Diffie-Hellman handshake proceeds as follows:
- Client hello: The client sends a message with the protocol version, the client random, and a list of cipher suites.
- Server hello: The server replies with its SSL certificate, its selected cipher suite, and the server random. In contrast to the RSA handshake described above, in this message, the server also includes the following (step 3):
- Server’s digital signature: The server computes a digital signature of all the messages up to this point.
- Digital signature confirmed: The client verifies the server’s digital signature, confirming that the server is who it says it is.
- Client DH parameter: The client sends its DH parameter to the server.
- Client and server calculate the premaster secret: Instead of generating the premaster secret and sending it to the server, as in an RSA handshake, the client and server use the DH parameters they exchanged to calculate a matching premaster secret separately.
- Session keys created: Now, the client and server calculate session keys from the premaster secret, client random, and server random, just like in an RSA handshake.
- The client is ready: Same as an RSA handshake.
- Server is ready
- Secure symmetric encryption achieved
*DH parameter: DH stands for Diffie-Hellman. The Diffie-Hellman algorithm uses exponential calculations to arrive at the same premaster secret. The server and client each provide a parameter for the calculation, and when combined, they result in a different calculation on each side, with equal results.
To read more about the contrast between ephemeral Diffie-Hellman handshakes and other kinds of handshakes, and how they achieve forward secrecy, see What is Keyless SSL?
What is different about a handshake in TLS 1.3?
TLS 1.3 does not support RSA, nor other cipher suites and parameters that are vulnerable to attack. It also shortens the TLS handshake, making a TLS 1.3 handshake both faster and more secure.
The basic steps of a TLS 1.3 handshake are:
- Client hello: The client sends a message with the protocol version, the client random, and a list of cipher suites. Because support for insecure cipher suites has been removed from TLS 1.3, the number of possible cipher suites is vastly reduced. The client hello also includes the parameters that will be used for calculating the premaster secret. Essentially, the client assumes that it knows the server’s preferred key exchange method (which, due to the simplified list of cipher suites, it probably does). This cuts down the overall length of the handshake — one of the essential differences between TLS 1.3 handshakes and TLS 1.0, 1.1, and 1.2 handshakes.
- The server generates a master secret: The server has received the client randomly and the client’s parameters and cipher suites. It already has the server random since it can generate that independently. Therefore, the server can create the master secret.
- Server hello and “Finished”: The server hello includes the server’s certificate, digital signature, server random, and chosen cipher suite. Because it already has the master secret and sends a “Finished” message.
- Final steps and client “Finished”: Client verifies signature and certificate, generates master secret, and sends “Finished” message.
- Secure symmetric encryption achieved
0-RTT mode for session resumption
TLS 1.3 also supports an even faster version of the TLS handshake that does not require round trips or back-and-forth communication between client and server. If the client and the server have connected before (as in, if the user has visited the website before), they can each derive another shared secret from the first session, called the “resumption main secret.” The server also sends the client a session ticket during this first session. The client can use this shared secret to send encrypted data to the server on its first message of the next session, along with that session ticket. And TLS resumes between the client and server.
What is a cipher suite?
A cipher suite is a set of algorithms for establishing a secure communications connection. There are several cipher suites in wide use, and an essential part of the TLS handshake is agreeing upon which cipher suite will be used for that handshake.