Attack vectors are how attackers can breach sensitive data or compromise an organization.
What is an attack vector?

An attack vector, or threat vector, is a way for attackers to enter a network or system. Common attack vectors include social engineering attacks, credential theft, vulnerability exploits, and insufficient protection against insider threats. A significant part of information security is closing off attack vectors whenever possible.
Suppose a security firm is tasked with guarding a rare painting that hangs in a museum. There are several ways that a thief could enter and exit the museum — front doors, back doors, elevators, and windows. A thief could enter the museum another way, perhaps by posing as a museum staff member. These methods represent attack vectors, and the security firm may try to eliminate them by placing security guards at all doors, putting locks on windows, and regularly screening museum staff to confirm their identity.
Similarly, digital systems all have areas attackers can use as entry points. Because modern computing systems and application environments are so complex, closing off all attack vectors is typically impossible. However, strong security practices and safeguards can eliminate most attack vectors, making it far more difficult for attackers to find and use them.
What are some of the most common attack vectors?
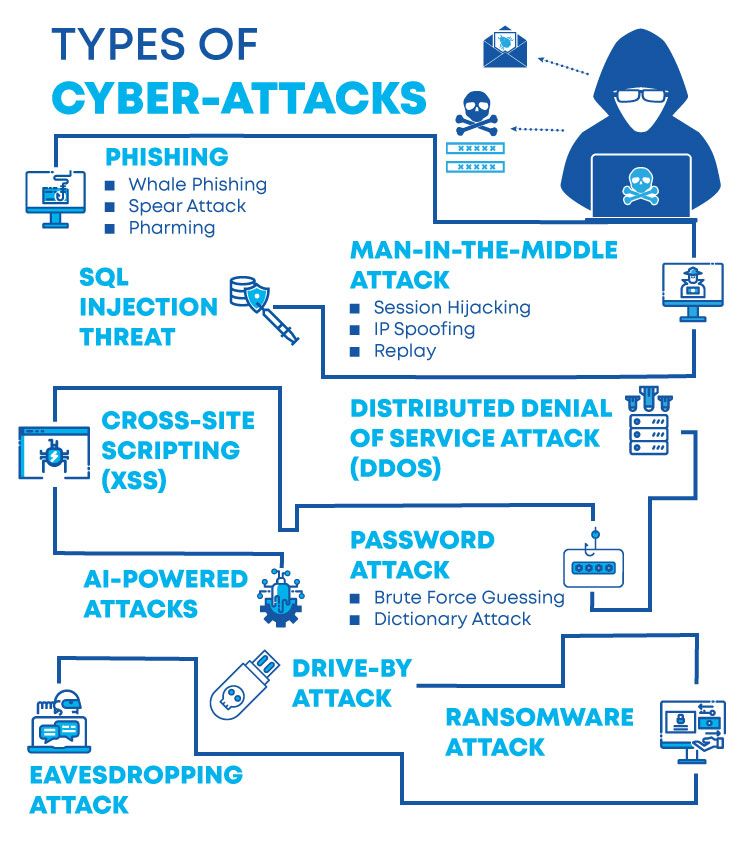
Phishing involves stealing data, such as a user’s password, that an attacker can use to break into a network. Attackers gain access to this data by tricking the victim into revealing it. Phishing remains one of the most commonly used attack vectors — many ransomware attacks, for instance, start with a phishing campaign against the victim organization.
Email attachments: One of the most common attack vectors, email attachments can contain malicious code that executes after a user opens the file. Multiple major ransomware attacks have used this threat vector in recent years, including the Ryuk attacks.
Account takeover: Attackers can control a legitimate user’s account using several methods. They can steal a user’s credentials (username and password) via phishing attacks, brute force attack, or purchasing them on the underground market. Attackers can also try intercepting and using a session cookie to impersonate a web application user.
Lack of encryption: Unencrypted data can be viewed by anyone with access to it. It can be intercepted in transit between networks, as in an on-path attack, or viewed inadvertently by an intermediary along the network path.
Insider threats: An insider threat is when a known and trusted user accesses and distributes confidential data or enables an attacker to do the same. Such occurrences can be intentional or accidental on the user’s part. External attackers can try to create insider threats by contacting insiders directly and asking, bribing, tricking, or threatening them into providing access. Sometimes, malicious insiders act of their own accord, out of dissatisfaction with their organization, or for other reasons.
Vulnerability exploits: A vulnerability is a flaw in software or hardware — think of it as a lock that does not work properly, enabling a thief who knows where the faulty lock is to enter a secured building. When an attacker successfully uses a vulnerability to enter a system, this is called a vulnerability “exploit.” Applying the software or hardware vendor’s updates can fix most vulnerabilities. But some are “zero-day” vulnerabilities — unknown vulnerabilities for which no known fix exists.
Browser-based attacks: To display webpages, Internet browsers load and execute code they receive from remote servers. Attackers can inject malicious code into a website or direct users to a fake website, tricking the browser into executing code that downloads malware or otherwise compromises user devices. With cloud computing, employees often access data and applications solely through their Internet browser, making this threat vector of particular concern.
Application compromise: Instead of going after user accounts directly, an attacker may aim to infect a trusted third-party application with malware. Or they could create a fake, malicious application that users unknowingly download and install (a common attack vector for mobile devices).
Open ports: A port is a virtual entryway into a device. Ports help computers and servers associate network traffic with a given application or process. Ports that are not in use should be closed. Attackers can send specially crafted messages to open ports to compromise the system, just as a car thief might try opening doors to see if any are unlocked.
How can an organization secure its attack vectors?
There is no way to eliminate attack vectors. But these approaches can help stop both internal and external attacks.
- Good security practices: Many attacks succeed due to user error: users fall for phishing attacks, open malicious email attachments, or provide access to an unauthorized person. Training users to avoid these errors can go a long way toward eliminating several major attack vectors.
- Encryption: Encrypting data in transit prevents it from being exposed to intermediary parties.
- Browser isolation: This technology loads and executes untrusted code to a location outside an organization’s secured network. Browser isolation can even help eliminate the threat of zero-day attacks, at least in the browser.
- Patching vulnerabilities: Many attacks occur because an organization has not patched a vulnerability. Patching vulnerabilities and regularly updating software and hardware vastly reduces the chances of a successful vulnerability exploit.
- Secure access service edge (SASE): As reliance on the cloud has changed corporate computing models, many organizations find their networking and security models must also change. Secure access service edge (SASE) is one method of integrating networking and security. SASE includes several security safeguards that close off the attack vectors described above — learn more about SASE.
What is an attack surface?
An attack surface combines all attack vectors available to an attacker. The more attack vectors an organization has, the greater the attack surface. Conversely, an organization can reduce its attack surface by eliminating attack vectors.
Think of an attacker as an offensive player in association football (soccer), and the attack surface as the goal. Without a goalkeeper, the front of the goal presents a relatively large area for the player to kick the ball through. However, the goalkeeper reduces the space available to the offense by positioning themselves strategically, and the goalkeeper’s teammates may do the same by how they defend.
Similarly, all organizations have a “goal” that external attackers target: the attack surface and the sensitive data behind it. But security products and practices are like goalkeepers and defenders, keeping attackers from using those vectors.