BGP hijacking is a malicious rerouting of Internet traffic that exploits the trusting nature of BGP, the routing protocol of the Internet.
What Is BGP Hijacking?
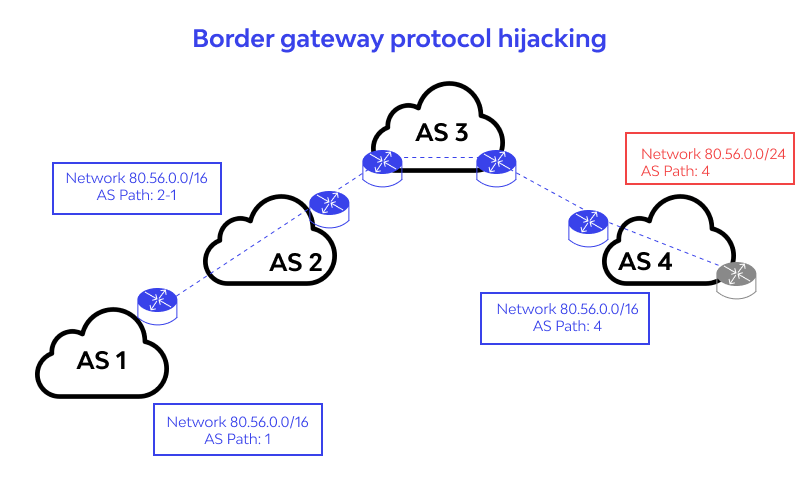
BGP hijacking is when attackers maliciously reroute Internet traffic. Attackers accomplish this by falsely announcing ownership of groups of IP addresses, called IP prefixes, that they do not own, control, or route to. A BGP hijack is much like if someone were to change out all the signs on a stretch of freeway and reroute automobile traffic onto incorrect exits.

Because BGP is built on the assumption that interconnected networks are telling the truth about which IP addresses they own, BGP hijacking is nearly impossible to stop – imagine if no one was watching the freeway signs. The only way to tell if they had been maliciously changed was by observing that many automobiles ended up in the wrong neighborhoods. However, for a hijack to occur, attackers need to control or compromise a BGP-enabled router that bridges one autonomous system (AS) and another, so not just anyone can carry out a BGP hijack.
What is BGP?
BGP stands for Border Gateway Protocol, and it is the routing protocol of the Internet. In other words, it provides directions so traffic travels from one IP address to another as efficiently as possible. An IP address is the actual web address of a given website. When a user types in a website name and the browser finds and loads it, requests and responses go back and forth between the user’s IP address and the IP address of the website. DNS (domain name system) servers provide the IP address, but BGP provides the most efficient way to reach that IP address. If DNS is the Internet’s address book, then BGP is the Internet’s road map.
Each BGP router stores a routing table with the best routes between autonomous systems. These are updated almost continually as each AS* – often an Internet service provider (ISP) – broadcasts new IP prefixes they own. BGP always favors the shortest and most direct path from AS to AS to reach IP addresses via the fewest possible hops across networks. Learn more about BGP >>
*Definition of an autonomous system (AS)
An autonomous system is a large network or group of networks managed by a single organization. An AS may have many subnetworks but share the same routing policy. Usually, an AS is either an ISP or a very large organization with its network and multiple upstream connections from that network to ISPs (this is called a ‘multihomed network’). Each AS is assigned its own Autonomous System Number, or ASN, to identify them easily. Learn more about autonomous systems >>
Why is BGP important?
BGP makes the large-scale growth of the Internet possible. The Internet is made up of multiple large networks that are interconnected. Because it is decentralized, no governing body or traffic cop is laying down the best routes for data packets to travel to their intended IP address destinations. BGP fulfills this role. If not for BGP, web traffic could take huge amounts of time to reach its destination due to inefficient routing or would never reach the intended destination at all.
How can BGP be hijacked?
When an AS announces a route to IP prefixes that it does not control, this announcement, if not filtered, can spread and be added to routing tables in BGP routers across the Internet. Until somebody notices and corrects the routes, traffic to those IPs will be routed to that AS. It would be like claiming territory if there were no local government to verify and enforce property deeds.
BGP always favors the shortest, most specific path to the desired IP address. For the BGP hijack to be successful, the route announcement must either:
1) Offer a more specific route by announcing a smaller range of IP addresses than other ASes had previously announced.
2) Offer a shorter route to certain blocks of IP addresses. Additionally, not just anyone can announce BGP routes to the larger Internet. For a BGP hijack to occur, the announcement must be made by the operator of an AS, or by a threat actor who has compromised an AS (the second case is rare).

It may seem surprising that the operator of a large network or group of networks, many of which are ISPs, would brazenly undertake such malicious activity. But considering that by some counts, there are now over 80,000 autonomous systems globally, it is not surprising that some would be untrustworthy. Additionally, BGP hijacking is not always obvious or easy to detect. Bad actors may camouflage their activity behind other Autonomous Systems (ASes) or announce unused blocks of IP prefixes that are not likely to be noticed to stay under the radar.
What happens when BGP is hijacked?
As a result of BGP hijacking, Internet traffic can go the wrong way, be monitored or intercepted, be ‘black holed,’ or be directed to fake websites as part of an on-path attack. In addition, spammers can use BGP hijacking, or the network of an AS that practices BGP hijacking, to spoof legitimate IPs for spamming purposes. From a user perspective, page load times will increase because requests and responses will not follow the most efficient network route and may even travel across the world unnecessarily.
In the best-case scenario, traffic would take an unnecessarily long route, increasing latency. In a worst-case scenario, an attacker could conduct an on-path attack or redirect users to fake websites to steal credentials.
BGP hijacking in the real world
There have been many real-world examples of deliberate BGP hijacking. For instance, in April 2018, a Russian provider announced several IP prefixes (groups of IP addresses) that belong to Route53 Amazon DNS servers. In short, the result was that users attempting to log in to a cryptocurrency site were redirected to a fake version of the website controlled by hackers. The hackers were thus able to steal approximately $152,000 in cryptocurrency. (To get more specific: Via BGP hijacking, the hackers hijacked Amazon DNS queries so that DNS queries for myetherwallet.com went to servers they controlled, returned the wrong IP address, and directed HTTP requests to the fake website.
Inadvertent instances of BGP hijacking are also prevalent and can harm the entire global Internet. In 2008, the Pakistani government-owned Pakistan Telecom attempted to censor YouTube within Pakistan by updating its BGP routes for the website. Seemingly on accident, the new routes were announced to Pakistan Telecom’s upstream providers and broadcast to the whole Internet. Suddenly, all web requests for YouTube were directed to Pakistan Telecom, resulting in an hours-long outage of the website for almost the entire Internet and overwhelming the ISP.
How can users and networks defend themselves from BGP hijacking?
Aside from constant monitoring of how Internet traffic is routed, users and networks can do very little to prevent BGP hijacks.
IP prefix filtering
Most networks should only accept IP prefix declarations if necessary and should only declare their IP prefixes to certain networks, not the entire Internet. Doing so helps prevent accidental route hijacking and could keep the AS from accepting bogus IP prefix declarations; however, this is difficult to enforce in practice.
BGP hijacking detection
Increased latency, degraded network performance, and misdirected Internet traffic are all possible signs of a BGP hijack. Many larger networks will monitor BGP updates to ensure their clients do not face latency issues, and a few security researchers monitor Internet traffic and publish their findings.
Making BGP more secure
BGP was designed to make the Internet work, and it certainly does that. But BGP was not designed with security in mind. More secure routing solutions for the Internet (such as BGPsec) are being developed, but there is no adoption of them yet. For the time being, BGP is inherently vulnerable and will remain so.